In this post, you’ll find how to structure the ethical hacking process to work in an organized, effective, and professional manner.
Ethical Hacking Process Steps
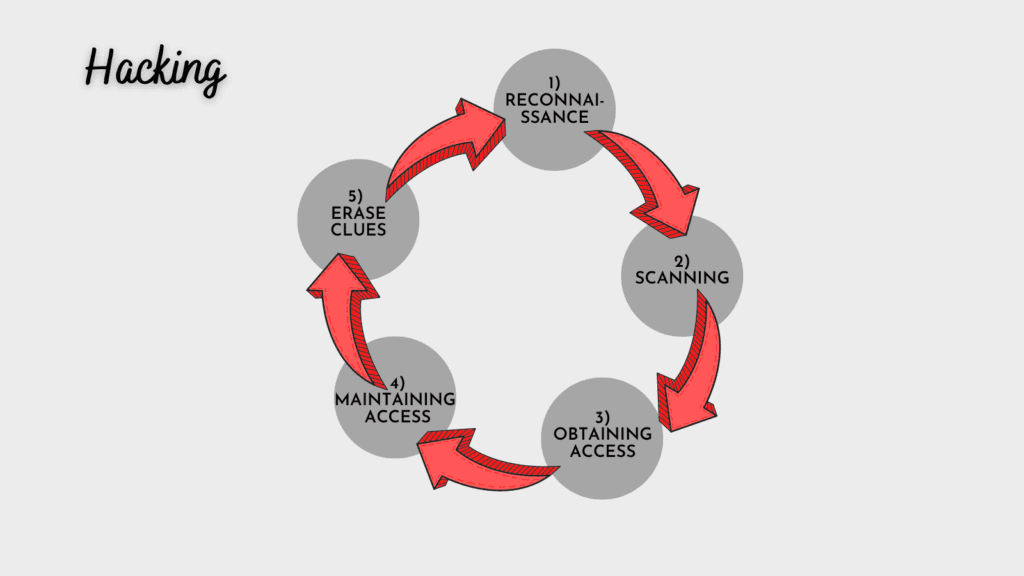
A hacker follows a structured process that contains 5 steps to achieve its purpose:
The process implemented by ethical hackers is similar with a slight variation:
- Pre-engagement
- Reconnaissance (passive and active)
- Scanning
- Gaining Access
- Reporting
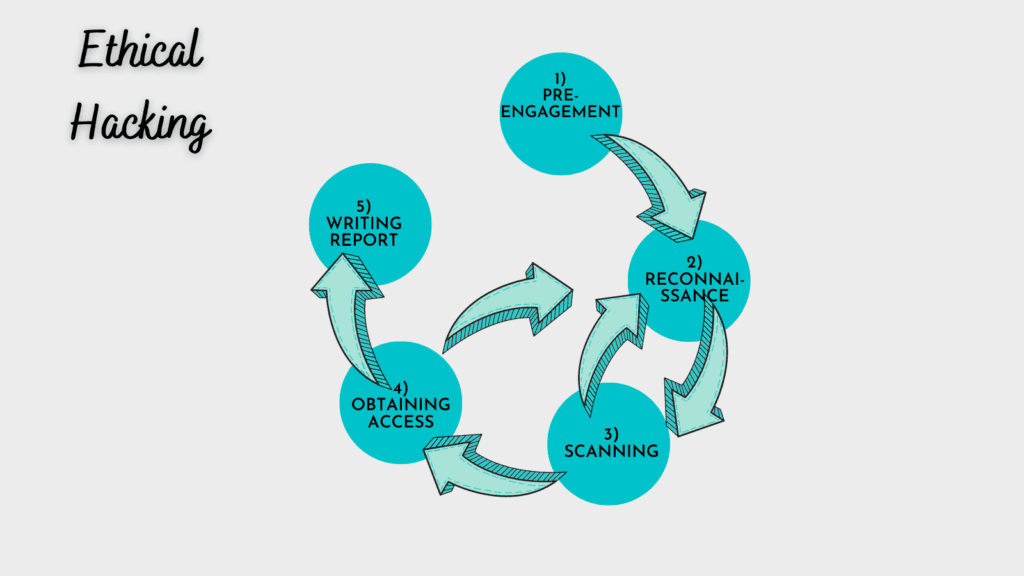
In this way, ethical hackers stop in Phase 3 of the hacking process to report their findings and make recommendations to the client in a final report.
In the following sections, we explain each of the ethical hacking steps.
1. Pre-Engagement
An ethical hacking project begins with a pre-engagement phase. It involves talking to the client to determine the goals, the scope of the project, obligations, and responsibilities.
Goals
In this step, you should ask why they want to do ethical hacking. For example,
- do they have any compliance focus? such as credit cards.
- do you need to take special care of any devices when testing?
- are there any particular assets they are worried about?
- do they want to test their detection capabilities?
You should focus on understanding your client’s business and the needs that you have to fulfill in the project.
Legal Aspects
After you agree on the formalities with the client, you can begin the ethical hacking process.
Be careful, do not begin before that. You must have the legal aspects, such as “permission to hack” and a “non-disclosure” agreement, signed by both parties.
Another important point is that you must be sure you have the authorization to perform ethical hacking on the target.
For example, if your client has their servers hosted by a third party, and you proceed with the ethical hacking. Then, you are attacking the hosting company and not your client. Hence, the authorization will not be valid. You must verify that the client has formal approval from the third party to perform the test.
Also, make sure your contract includes a statement that limits your liability in case something unexpected happens.
Scope
The scope limits the dimension of the projects. The objective is to understand which components or hosts you have to test and what is out of scope.
In addition, determine the techniques that you should use: social engineering, wireless security, how deep should be web scanning, etc.
Allowed techniques
Ask about the methodologies that you can use. For example, exploits may potentially bring down a service, does the client agree with that?
Vulnerability Assessments VS. Ethical hacking
Often, a vulnerability assessment is confused with ethical hacking. However, these terms have completely different meanings.
A vulnerability assessment finds out all the vulnerabilities in an asset and documents them.
Ethical hacking simulates the attack to test if you can exploit a vulnerability, and document the vulnerabilities that were exploited and the ones that turned out to be false positives.
It is important to understand what the client expects us to do. Does the client merely expect you to detect possible vulnerabilities?
Risks and Responsibilities
It’s important to be aware of the risks and take the appropriate prevention actions. For example, the client has to understand that even a simple port scan could bring down a server or router.
You have to inquire about any fragile system or critical components for business operations. Then, formulate a plan to address them in case of unexpectedly shut down, restarted, or slow down.
The liabilities and responsibilities should be decided ahead of time.
As an ethical hacker, you might break into something that should not be accessible, causing a denial of service, or you might access sensitive information such as credit cards. Therefore, the liabilities should be defined before the engagement.
Testing Time
You should ask if the client wants you to perform tests only during specific hours or on certain days to mitigate the risks of system failure due to the tests.
Contact
Before starting the project, you have to agree on how to communicate relevant and sensible information. For example, if you find something serious, to whom should you report it?
It is also important to set up secure communication channels with your client, for example, encrypted email.
Also, protect the output information from your testing:
- Ensure your document repository is secure.
- Set up multifactor authentication on your e-mail, document repository, and anything that allows remote access to your working environment.
Describe your methodology in detail to your client and negotiate the rules of engagement. For example, if they can try to stop your attack emulation if they detect it, who should know about the testing, etc.
Lastly, remain accountable for your actions. Log and document all your testing activities. You can read more about how to do this in the post on how to document your ethical hacking process.
Duration and Payment
Finally, you should establish the project duration, including both the start and the end date. Negotiate how, when, and how much they will pay you.
2. Reconnaissance
This phase is also called footprinting, information gathering, or open-source intelligence (OSINT).
This is the step of the ethical hacking process where you gather information about your target. There are two reconnaissance types: passive and active reconnaissance.
Passive Reconnaissance
This kind of reconnaissance collects information about the target without directly accessing it. This involves collecting information from publically available resources to gather information about the company, its systems, and its employees.
The chances of getting discovered in passive reconnaissance are extremely low since you will be primarily leveraging publicly available information.
Passive reconnaissance activities may include, but it’s not limited to, the identification of:
- IP Addresses
- Domains and subdomains
- Company locations and branches
- Other companies with which the target company partners or deals
- People (company contact names, phone numbers, and email addresses)
- Technologies
- Content of interest
- Company privacy policies.
None of these techniques involve intrusive scanning or probing the system. Instead, all the information is gathered from Google, public sites, social networks, social engineering, online databases, dumpster diving, etc. using existing techniques and tools.
Active Reconnaissance
During active reconnaissance, you directly interact with the target to gather information about it.
For example, probing the network to discover individual hosts, IP addresses, open services, enumerate services (such as DNS, SMTP, SNMP, SMB), and operative systems.
This process involves more risk of detection than passive reconnaissance.
Active reconnaissance can give a hacker an indication of security measures in place, but the process also increases the chance of being caught or at least raising suspicion.
You need to be careful not to cause too much noise on the network to avoid detection by Intrusion Detection Systems.
Many software tools that perform active reconnaissance can be traced back to the computer that is running the tools, thus increasing the chance of detecting the hacker.
Both passive and active reconnaissance can lead to the discovery of useful information to use in an attack.
For example, it’s usually easy to find the type of web server and the operating system (OS) version number that a company is using. This information may enable a hacker to find a vulnerability in that OS version and exploit the vulnerability to gain access.
In summary, active reconnaissance relies on traffic being sent to the targeted machine. However, passive reconnaissance uses the information you can accumulate from the Internet. For that reason, the passive strategy is de facto undetectable, and the active one may be noticed and tracked.
This is by far the most time-intensive step when performing ethical hacking, as you want to be aware of all the attack vectors that can be leveraged.
3. Scanning
In this phase, you begin to actively probe a target machine or network to find vulnerabilities that can be exploited.
Scanning involves checking the target system for weaknesses that may be exploited.
This task can be done manually or with help of automated tools.
4. Gaining Access
In this step, you attempt to exploit the vulnerabilities you have found in the previous phase and enter into the system using different tools.
After entering into a system, you may want to increase your privilege to the administrator level to be able to perform more actions in the system.
Also, you should try to make a lateral movement to compromise other systems in the network.
5. Reporting
Reporting is the last step in the ethical hacking process.
Here, the ethical hacker creates a report with his findings, suggestions to improve the system’s cybersecurity, and the job that was done, such as the tools used, the success rate, vulnerabilities found, and the exploit processes.
Maintaining Access
This phase does not exist in the ethical hacking process, but is executed during an attack. I mention it because it is important to know it and create configurations and policies to prevent it.
After gaining access, a hacker wants to maintain that access. For example, installing some backdoors to enter into the system when needed in the future.
This step usually involves installing software or making configuration changes to ensure access can be gained later.
Clearing Tracks
This process is also an unethical activity that exists in the attack process and should be prevented in the configuration of the systems. It aims at clearing all evidence, so, no one will find any traces leading to the attacker.
For example, delete, corrupt, or modify logs of all the activities that take place during the hacking process.
Also, it may include:
- modify registry values,
- uninstall all applications used,
- delete or hide all created folders,
- clear out sent emails, temp files, or intrusion detection system (IDS) alarms,
- hide the active processes that allow the attacker to regain access,
- disable messages to security software
- or delete email alerts of possible unauthorized logins.
Final Words About the Ethical Hacking Steps
To sum up, compromising a system requires a series of steps to identify vulnerabilities and exploit them. In this post, we explained a structured methodology to do this task. Find more information about the ethical hacking steps and tools to implement them in our free ethical hacking course.
Follow us
Related post that may interest you



